EXHIBITION OBJECTS
Trust is the staple of our diet; responsibility is something we as users can choose to assume or not; promises are meant to be kept, and anger and powerlessness are what we feel as a result of the constant abuse of our trust.
Anger & Powerlessness | Trust | Promises | Responsibility

Anger & Powerlessness
I got back to class and sat down again, Ms Galvez warmly welcoming me back. I unpacked the school’s standard-issue machine and got back into classroom mode. The SchoolBooks were the snitchiest technology of them all, logging every keystroke, watching all the network traffic for suspicious keywords, counting every click, keeping track of every fleeting thought you put out over the net. We’d gotten them in my junior year, and it only took a couple months for the shininess to wear off. Once people figured out that these “free” laptops worked for the man – and showed a never-ending parade of obnoxious ads to boot – they suddenly started to feel very heavy and burdensome. ( Cory Doctorow)
GAFAM
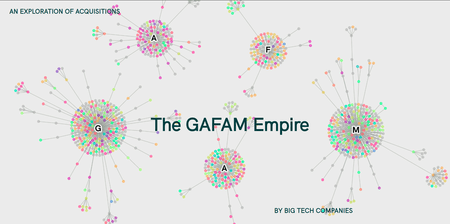
From the second half of the 70s, the world witnessed the birth and affirmation of the so-called Big Tech, the five largest companies that operate in the field of information technology. Also known as “GAFAM” (acronym of Google, Apple, Facebook, Amazon and Microsoft), in the last fifty years they were able to build empires of intellectual properties of technologies and systems through acquisitions of other companies small and large, centring technological innovations within their walls. “GAFAM Empire”, a project developed by DensityDesign Lab and Tactical Tech, collects the information of more than a thousand acquisitions, to have a look back on the history of the industry through limited data publicly available on the web. Thanks to them, a landscape of acquisitions is built to identify common interests that are then broken down into a deep analysis of GAFAM’s history. The project visualises the data with different shapes and through different focuses, allowing the reader to understand a complex system of relationships that is constantly evolving and that is redefining the concepts of competitions and monopoly.
Google Society
by La Loma and Tactical Tech
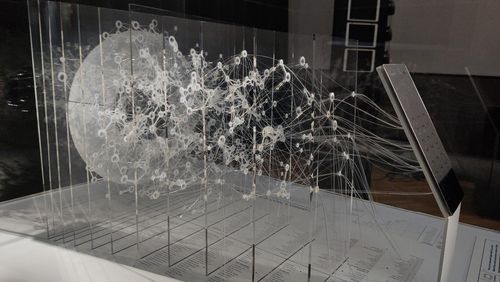
You are most likely a Google user. Even if you don’t use gmail, it’s likely that you use at least one of the more than 295 products that Google owns. That might not sound like a big deal, until you consider that there are billions of people around the world like you, who depend on Google’s services and whose data Google can access and analyse. The more data Google collects through its suite of products, the more powerful the nsights it can glean about entire populations. It can be hard to quantify exactly how much of the world’s population depends on Google, but by looking at how many users each of their products has, we can begin to extrapolate. This piece visualises the depth and reach of Google and its suite of 295 products and services. It asks you to think about how far Google extends into your daily life, and, in turn, to the billions of other people’s lives who rely on the same products you do, and how, ultimately, this contributes to the growth and revenue of the company.
Amazonification
by La Loma and Tactical Tech

Although Jeff Bezos has promised to make Amazon “Earth’s Best Employer,” the past few years have seen an increasing number of scandals around Amazon’s work practices – from patents for worker ‘cages’ to stories of labour organizers being surveilled.
In a quest to fulfil demand and achieve worker optimization, Amazon has patented a number of innovative – and controversial – ideas for the workplace. This piece shows Amazon’s patents for wearable technologies designed for workers. These devices are designed to maximize efficiency and speed, while minimizing costs and reducing friction between humans and robots.
The patents give us insight into the company’s vision of ‘optimization’: the introduction of more and more systems to monitor and automate human behaviour. These technologies and practices are increasingly becoming the norm not just at Amazon, but at other companies that want to compete with Amazon’s speed, efficiency and profit. When we want our products quickly and cheaply, what are the consequences for workers?
Luminosity
by Marlene Lerperger

On March 9 2018, Science Magazine published an article about the circulation of true and false news on Twitter. “When we estimated a model of the likelihood of retweeting, we found that falsehoods were 70% more likely to be retweeted than the truth.”
The design object illustrates how much faster and more frequent falsehoods are being spread as opposed to the truth. The luminous circles represent tweets shared by users who are depicted as rays. On the left-hand side there are only 5 rays per circle. This means that 5 people shared the tweet. On the right-hand side there are alternately 8 and 9 rays per circle. In this case, the tweet is shared 8 or 9 times meaning that compared to the truth, the rate at which falsehood is retweeted is 70% higher. The illustration reveals the problematic nature of news distribution on the Internet. The bright luminescence of the graphics representing fake news ought to be a wake-up call for us all. The amount of lies and fake news circulating on the Internet is huge. We should not only consume and spread news but also question them and keep an open and critical mind when surfing the Internet.
Responsibility
If we were to accept that we bear responsibility we would see a lot of processes in a different light. Our leisure activities, our communication, our political attitude, our buying behaviour, our search queries, our finances, our fashion style … all of it is connected and interlinked – also for corporations such as Google analysing all of it and drawing conclusions as to which advertiser ought to show us what. By identifying these links, we will be able to make free and autonomous decisions. (Klaudia Zotzmann-Koch)
100+ Protests
by La Loma und Tactical Tech

As tech companies have grown and expanded their global reach, there has been increasingly visible backlash and resistance against their practices from both inside and outside the industry.
This timeline highlights more than 100 protests over the last ten years selected from publicly available information. It offers a view into the consequences of tech companies’ decisions, policies, and practices and their impact on their workforce, users, contractors, vendors, clients, and customers. The timeline also reveals the recent trend toward collective worker resistance within Big Tech. Some of these protests have yielded attention and results, while others have flown under the radar or been overlooked by the media. With governments slow to regulate, and companies reluctant or failing at selfregulation, could these protests point toward a form of accountability?
Data Detox Bar
by Tactical Tech

At this Bar visitors can pick up a copy of the Data Detox Kit. The Data Detox Kit includes everyday steps you can take to control your digital privacy, security, and wellbeing in ways that feel right to you.
Within the kit, you will find four guides to get you started:
- SMARTPHONE ANTIOXIDANTS - Control Your Smartphone Data to Increase Your Online Privacy
- A ZEST FOR LIFE BALANCE – Escape the Defaults to Enhance Your Digital Wellbeing
- KNOWLEDGE CONCOCTIONS - 6 Tips to Steer Clear of Misinformation Online
- SETTINGS WITH A TWIST - Shift Your Settings to Secure Your Data
The Ridiculous Scale of Responsibility
by Daniel Kranewitter
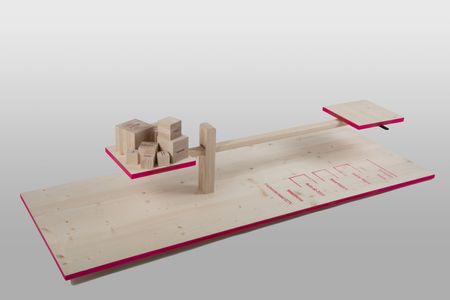
How much responsibility can I hand over? The Ridiculous Scale of Responsibility conveys the daily balancing act between private and public sphere on a human level of understanding. Certain objects allow us to trade data for convenience – but who is actually aware of that? Visitors are invited to try for themselves to keep the balance and see to what extent they are willing to give up their privacy in exchange for convenience.
Offline
by Olaf Osten

The series Offline consists of monochrome acrylic painting on digital tablets out of function and shows a sequence of landscapes and elements of cultural history. The digital (r)evolution has brought us an additional dimension of invisible space with a lot of possibilities – nevertheless “being Offline” by switching off the internet also seems to provide us with important moments of independence. How can we wisely take advantage of these ambivalent circumstances? When and where are we right here? When are we there? In which space do we have to be to gain room within ourselves? Where exactly do we find ourselves in case our www.-tool runs out of function? In yesterdays world? In the future? Or here and now?
Trust
We are confident that providers will pay careful attention to programmes, messengers, platforms and services and that they will for instance prevent any unauthorised access to read along. We post pictures trusting they will remain on the platform and that our followers will not pass them off as their own, save them, modify them, turn them into deepfakes or make use of them in other ways. Trust is not only a central component of human co-existence, but also the basic currency on the Internet – a monetary commodity. (Klaudia Zotzmann-Koch)
Virtual Peephole
von Caroline Buttet

There are an estimated 770 million surveillance cameras around the world. Some of them still have their default password, making them entirely accessible by anyone who has an internet connection.
Virtual peephole is a device to watch some of those unsecured cameras. Made of a common-looking wooden box, it contains a microcomputer and some electronics. At the centre of the box is a peephole. By leaning closer to the box, the viewer can look through the peephole and watch lunsecured live feeds from various camera locations.
Shops, beaches, offices, streets, rooftops, birds nests… Virtual Peephole can access thousands of different streams. By opening and closing the peephole’s lid, the user can manually switch cameras as if he was peeping through a door with an ever-changing scene.
In this installation, the viewer is placed in the position of the voyeur. Virtual Peephole is a hypnotic piece that brings up the topic of internet surveillance, cyber-security and digital presence.
WannaScry!
by Danja Vasiliev (The Critical Engineering Working Group)

illustrates a security breach of a video-calling service and demonstrates to the public the extent to which personal biometric data can be intercepted and extracted by malicious cyber-actors and state agencies.
The work seeks to draw attention to the next generation of our interrelationship with the internet and vulnerabilities that come with our accelerating sublimation into cyberspace.
Taking the shape of a large scrying ball on the surface of which images of intercepted video-calls are projected, WannaScry! installation references “remote viewing” - known as an extrasensory ability, today is easily afforded by the functional principals of the internet.
While displaying contents of each video call, WannaScry! attempts to extract facial (biometric) and conversational (sentiment and context) data of those individuals participating in the call, including their geographic location. That information is then relayed visually to the audience.
The Real Live of Your Selfie
by Tactical Tech
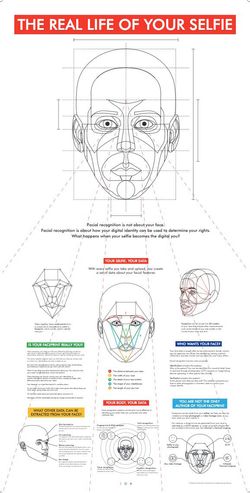
With every selfie you take and upload, you automatically create a set of data about your facial features. Taken together, different nodal points for a unique set of characteristics called a faceprint. A faceprint can be used to identify you, but is your faceprint really you? Facial recognition makes life more convenient by allowing us to quickly unlock our phones, pay for services and goods and open doors; it’s a process which seems relatively harmless, but what happens when your faceprint is used to measure your emotions and monitor your behaviour?
Facial recognition is actually not about your face. Facial recognition is about how your digital identity can be used to determine your rights. What happens when your selfie becomes the digital you?
Your Phone Number Is Not Only Yours
by Tactical Tech
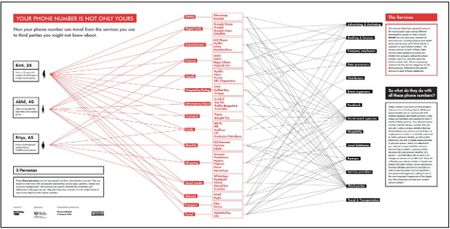
How your phone number can travel from the services you use to third parties you might not know about.
Today a phone is as much a communication device as it is a tracking device. While your phone enables you to communicate with endless analogue and digital services, it also makes you traceable and exposed to many if not all of these services. Your device’s phone number, besides being a number that one can call, is also a unique identifier that can travel between your devices and activities.
A single phone number is a valuable asset used to verify a person’s identity, as well as their behaviour, not only in digital spaces but also in physical spaces. When it is attached to your device’s unique identifier and your personal log in details, a phone number becomes the most precise identifier of a person – one that stays with us even if we change our phone or our SIM card. Once it’s collected, your phone number is shared and traded with other entities: direct subsidiaries, business affiliates and service providers as well as external parties such as advertisers and government agencies, making it one of the most important fingerprints of the digital
era. How long have you had your current phone number?
Promises
Eternal love, a slender waist, ethical data processing; being promised something triggers our trust mechanisms. As social beings we tend to believe promises. They make us feel good, a sentiment we associate with security. The advertising industry and big corporations have invested billions in order to find out how we think and come to decisions, what we click on, how we move online and offline and how our attention can be captured for as long as possible. Our brain functions are used against us for the maximisation of profits. (Klaudia Zotzmann-Koch)
Dictator Of Your Choice
Video installation by Gisela Schmalz


Director, Writer: Gisela Schmalz
Camera, Editor: Reinhard Mayr
Starring: Elena Hrncirik / Oskar Kozeluh
Vote while you still can. But who is up for election?
Two tech entrepreneurs are trying to win your vote. With their speeches, they compete for the dictatorship of the world society of the future. Both present their plans for shaping the new society using the latest technologies.
One candidate’s vision is more one of prosperity and pleasure, while the other candidate’s vision is primarily one of security and harmony. Both praise their model as the solution to all problems and themselves as the ideal leader.
Which dictator do you choose?
Slow Spending or the Bank is a Liar
by Seppo Gründler | Ushi Reiter | Eva Ursprung

With their installation Seppo Gründler, Ushi Reiter, Eva Ursprung raise the issue of digital interdependencies shaping our everyday life. We see a TAN generator which, although no longer fashionable, continues to be a secure way of carrying out digital bank transactions without requiring a smartphone. Online shopping becomes substantially slower with this payment method linked to a bank card. Prevalent are smartphones using equivalent bank Apps that are considered safe and secure. Customers rarely question the fact that they are at the same time forced into a dependency of big IT monopolists in the US. The reason why banks tend to keep quiet about alternatives is that this method opens up their technical interfaces to customer data to other companies and thus to a new business model.
With the old-fashioned TAN generator, transfers are exclusively made via the bank’s institute network meaning that there is no need for infrastructures outside the bank’s reach such as mobile phone networks.
How Your Phone is Designed to Grab your Attention
by Tactical Tech
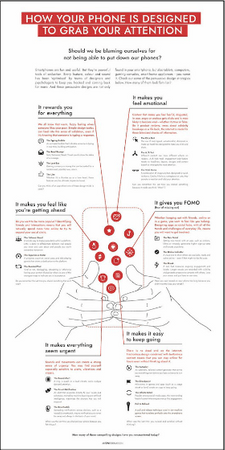
Are you finding it hard to put down your phone? When you feel your phone buzz, can you resist the urge to check it? It may not be obvious, but every feature, colour and sound on your smartphone has been optimised by teams of designers and psychologists to keep you coming back for more. Find out about some of the most common persuasive design strategies.
Parainformation
von Gerda Lampalzer
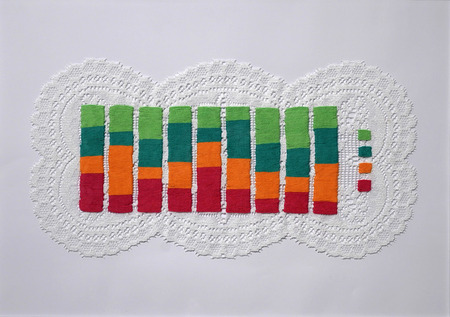
Parainformation is a series of works drawing on a display tool which has recently moved to the foreground of public attention: the diagram. Whereas in public communication diagrams are used to present information in an illustrative and generally comprehensible way, Gerda Lampalzer strips them of their meaning and examines them in terms of their formal aspect only. In order to do so she reverts to textile techniques increasingly discussed in a political context. Crocheted, knitted, embroidered and woven diagrams enter an astonishing link between apparent precision and individual forming. The result is an aesthetic disassociation inviting the viewer to imagine alternative bits of information. Parainformation plays with the connotations of scientific nature and subjectivity, of programme and handicraft, while remaining explicitly within the framework of media art.